Updated:
Skip to Promo Skip to main content Global Search US Store Login Cloud Services Console Customer Connect Partner Connect Multi-Cloud Services Products Solutions Partners Resources Main Menu Cloud Services Console Customer Connect Partner Connect Search GET STARTED Global Search Main Menu Todayâ s Multi-Cloud Reality : Cloud Chaos 87 of enterprises use two or more cloud environments to run their applications . Multi-cloud accelerates digital transformation , but also introduces complexity and risk , resulting in a chaotic reality for many . organizations LEARN ABOUT MULTI-CLOUD Conquer Cloud Chaos with VMware Cross-Cloud services VMware is addressing cloud chaos with our portfolio of multi-cloud services , VMware Cross-Cloud services , which enable you to build , run , manage , secure , and
Updated: 2024-01-31 02:00:02
, , : Internet Storm Center Sign In Sign Up Handler on Duty : Johannes Ullrich Threat Level : green previous ISC Stormcast For Wednesday , January 31st , 2024 https : isc.sans.edu podcastdetail 8832 previous Comments Login here to join the . discussion Top of page Ø Diary Archives Homepage Diaries Podcasts Jobs Data TCP UDP Port Activity Port Trends SSH Telnet Scanning Activity Weblogs Threat Feeds Activity Threat Feeds Map Useful InfoSec Links Presentations Papers Research Papers API Tools DShield Sensor DNS Looking Glass Honeypot RPi AWS InfoSec Glossary Contact Us Contact Us About Us Handlers About Us Slack Channel Mastodon Bluesky X 2024 SANS™ Internet Storm Center Developers : We have an API for you Link To Us About Us Handlers Privacy Policy
Updated: 2024-01-30 15:37:38
We use Cowrie to emulate an SSH and Telnet server for our honeypots. Cowrie is great software maintained by Michel Oosterhof [1]. The honeypot is a reasonable emulation of such a server, easy to maintain, and very feature-rich for even more advanced analysis. We only use it in its simplest form for our DShield sensor.
Updated: 2024-01-30 02:15:05
We use Cowrie to emulate an SSH and Telnet server for our honeypots. Cowrie is great software maintained by Michel Oosterhof [1]. The honeypot is a reasonable emulation of such a server, easy to maintain, and very feature-rich for even more advanced analysis. We only use it in its simplest form for our DShield sensor.
Updated: 2024-01-29 14:01:16
Last October, Atlassian released a patch for %%cve:2023-22515%% [1]. This vulnerability allowed attackers to create new admin users in Confluence. Today, I noticed a bit a "flare up" in a specific exploit variant.
Updated: 2024-01-29 02:15:04
Last October, Atlassian released a patch for %%cve:2023-22515%% [1]. This vulnerability allowed attackers to create new admin users in Confluence. Today, I noticed a bit a "flare up" in a specific exploit variant.
Updated: 2024-01-26 02:00:01
Windows batch files (.bat) are often seen by people as very simple but they can be pretty complex or.. contain interesting encoded payloads! I found one that contains multiple payloads decoded and used by a Powershell process. The magic is behind how comments can be added to such files. The default (or very common way) is to use the "REM" keyword. But you can also use a double-colon:
Updated: 2024-01-25 02:00:02
These days, many pieces of malware are flagged as “infostealers†because, once running on the victim's computer, they search for interesting data and exfiltrate them. Classic collected data are:
Updated: 2024-01-24 14:01:00
User interface design is one of those often overlooked aspects in software design in general. A bad user interface can quickly become a vulnerability regarding security. Even though I do not remember actual CVE&#;x26;#;39;s assigned to bad user-interface design, there probably should be some. One of the more famous user interface design issues was the "Therac-25" radiation treatment device. A bad user interface has been blamed for contributing to some deadly accidents [1].
Updated: 2024-01-18 23:07:40
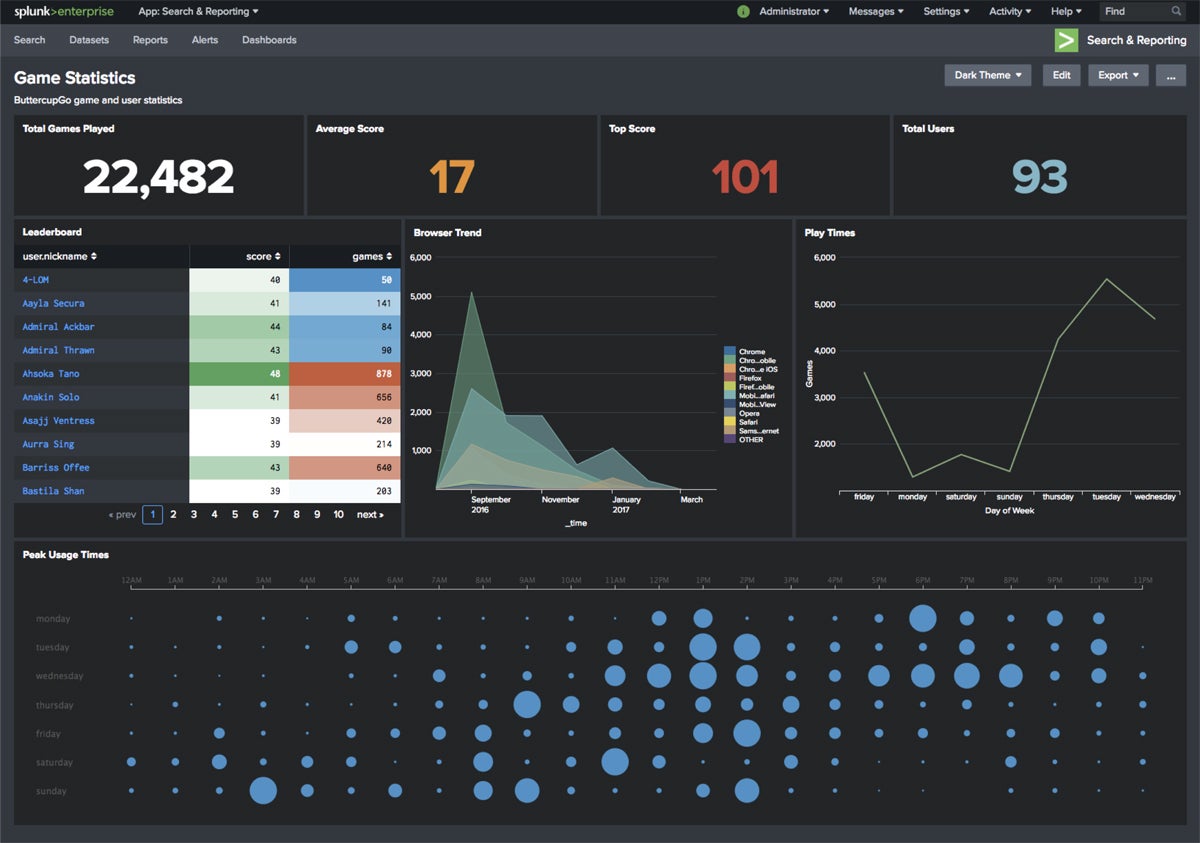
Learn the top AI data analytics software to use. Compare AI data analytics solutions & features to make the best choice for your business.
The post 8 Best AI Data Analytics Software & Tools of 2024 appeared first on eWEEK.
Updated: 2024-01-04 10:12:00

In this video I analyze a pcap file with network traffic from Cobalt Strike Beacon using CapLoader. The video cannot be played in your browser. The pcap file and Cobalt Strike malware config can be downloaded from Recorded Future's Triage sandbox. Cobalt Strike Beacon configs can also be extracted l[...]

 Learn the top AI data analytics software to use. Compare AI data analytics solutions & features to make the best choice for your business.
The post 8 Best AI Data Analytics Software & Tools of 2024 appeared first on eWEEK.
Learn the top AI data analytics software to use. Compare AI data analytics solutions & features to make the best choice for your business.
The post 8 Best AI Data Analytics Software & Tools of 2024 appeared first on eWEEK.
 In this video I analyze a pcap file with network traffic from Cobalt Strike Beacon using CapLoader. The video cannot be played in your browser. The pcap file and Cobalt Strike malware config can be downloaded from Recorded Future's Triage sandbox. Cobalt Strike Beacon configs can also be extracted l[...]
In this video I analyze a pcap file with network traffic from Cobalt Strike Beacon using CapLoader. The video cannot be played in your browser. The pcap file and Cobalt Strike malware config can be downloaded from Recorded Future's Triage sandbox. Cobalt Strike Beacon configs can also be extracted l[...]